Highlights
- The Dark Web is a hidden corner of the internet where cybercrime thrives.
- Hackers use techniques like phishing, social engineering, and malware to gain access to sensitive information.
- To protect yourself, educate yourself about the threats, use strong passwords, avoid clicking on suspicious links, and keep your software up-to-date.
- By taking these steps, you can reduce the risk of falling victim to cybercrime and protect your sensitive information.
- In this blog, we are taking a closer look at Dark Web and also understanding how to save yourself from hackers.
The Dark Web is a term used to describe the hidden corners of the internet that are not indexed by standard search engines. While the internet has revolutionized the way we access information and communicate with others, the Dark Web is home to many illegal activities, including cybercrime.

Hackers are constantly looking for ways to exploit vulnerabilities in computer systems, networks, and applications, and the Dark Web provides a fertile ground for them to find tools and resources to carry out their attacks. Cybercrime has become more sophisticated over the years, with hackers using techniques like phishing, social engineering, and malware to gain access to sensitive information.

To protect yourself from the dangers of the Dark Web, there are several steps you can take. The first step is to educate yourself about the threats that exist and the methods hackers use to carry out their attacks. This includes staying up-to-date with the latest security trends and being aware of the risks associated with using the internet.
Another way to protect yourself is to use strong passwords and enable two-factor authentication wherever possible. You should also avoid clicking on suspicious links or downloading attachments from unknown sources.
Moreover, it’s important to keep your computer and software up-to-date with the latest security patches and updates. This will help to prevent hackers from exploiting known vulnerabilities in your system.
In this blog, we are digging deep into how to save yourself from Hackers with a closer look at Dark Web. By the end of this post, you would learn about reducing the risk of falling victim to cybercrime and protecting your sensitive information from hackers on the Dark Web.
What is Dark Web?
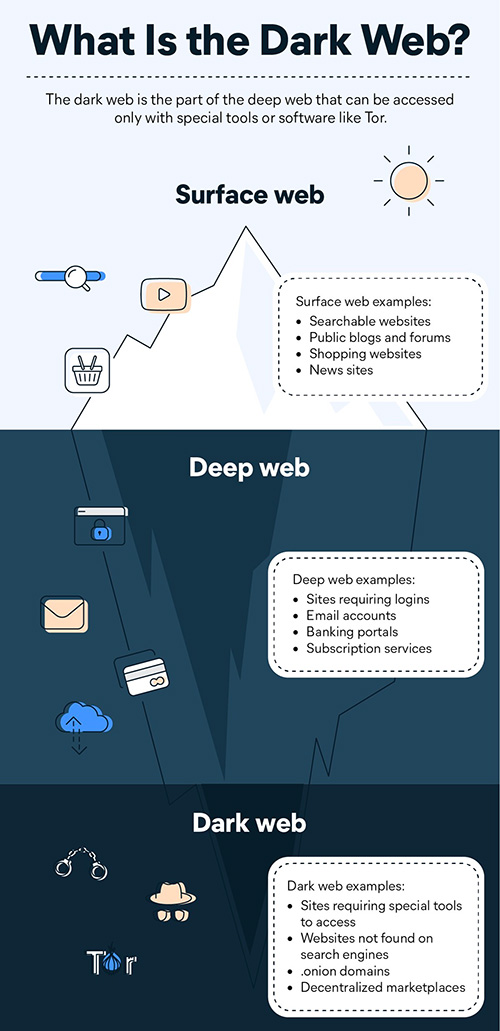
The Dark Web is a part of the internet that is not indexed by standard search engines such as Google or Bing. Instead, it is accessed through a special browser that allows users to browse anonymously and access websites that are not available on the open web.
The Dark Web is often associated with illegal activities, such as drug trafficking, weapons sales, and hacking services.
Unlike the open web, where websites are hosted on servers and their locations can be easily tracked, websites on the Dark Web are hosted on a network of servers and computers that are decentralized and difficult to trace. This makes it harder for law enforcement agencies to track down individuals involved in illegal activities on the Dark Web.
While the Dark Web is often portrayed as a dangerous place where criminals thrive, it is also used by activists, journalists, and whistleblowers who need to communicate anonymously and protect their identities.
However, it is important to note that accessing the Dark Web can be risky and should be done with caution, as it is possible to stumble upon illegal content or fall victim to cybercrime.
How to Access Dark Web & What Will You Find?
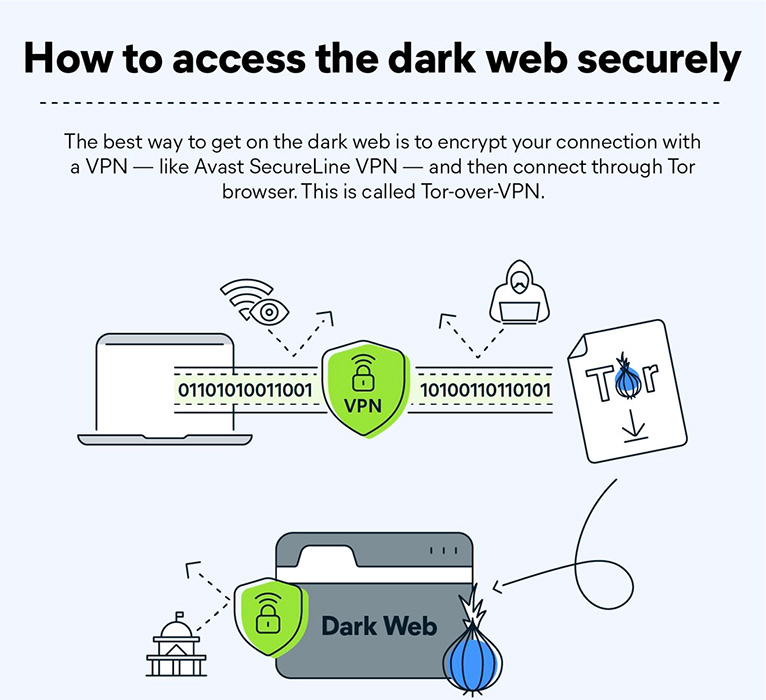
First things first, it is important to note that accessing the Dark Web can be risky, as it is possible to stumble upon illegal content or fall victim to cybercrime. Once you understand the risks involved, take a closer look at how to access Dark Web.
To access the Dark Web, you will need to download and install a special browser, such as Tor or I2P. These browsers allow you to access websites with .onion or .i2p domains, which are not available on the open web.
Steps to access the dark web using Tor browser

- Visit the Tor Browser website to download the latest Tor browser.
- Open the downloaded file and follow the prompts to install the Tor browser on your PC/laptop or Android mobile phone.
- Once installed, click on the Tor browser icon to open it.
- Tap the “Connect” button and wait for a connection to be established.
- Start surfing the dark web!
Once you have installed the Dark Web browser, you can start exploring the Dark Web.
One of the most well-known features of the Dark Web is its marketplaces, where users can buy and sell goods and services anonymously. These marketplaces can include anything from drugs and weapons to fake IDs and stolen credit card information. However, some marketplaces sell legal products, such as books and art.
Another popular feature of the Dark Web is its forums, where users can discuss a wide range of topics anonymously. These forums can cover anything from politics and religion to technology and hacking. While some of these forums can be used to facilitate illegal activities, such as sharing tips on how to carry out cybercrime, many of them are simply used for discussions on various topics.
In addition to marketplaces and forums, there are also websites on the Dark Web that provide anonymity and privacy services. These can include encrypted email services, virtual private networks (VPNs), and anonymous messaging apps. These services can be useful for individuals who are concerned about their privacy or want to communicate with others without revealing their identities.
What Is Found on the Dark Web?

It’s important to note that while the Dark Web does contain some legitimate and useful services, the majority of what can be found on the Dark Web is illegal or at least morally questionable. Accessing the Dark Web can be dangerous and should be done with caution, as it is possible to fall victim to cybercrime or stumble upon illegal content.
Here is a quick brief on what can be found on the Dark Web:

- Marketplaces for buying and selling illegal goods, such as drugs, weapons, and stolen credit card information
- Forums for anonymous discussion on a wide range of topics, including politics, religion, and technology
- Communication channels for individuals who want to communicate anonymously or protect their identities
- Websites offering anonymity and privacy services, such as encrypted email services and virtual private networks (VPNs)
- Hacking services and tutorials for individuals who want to learn how to carry out cybercrime
- Illegal pornography and other forms of illicit content
- Services for hiring hitmen, contract killers, and other criminals
- Counterfeit money and fake IDs
- Tutorials and guides for carrying out illegal activities, such as identity theft and credit card fraud
- Whistleblower sites for individuals who want to leak sensitive information without being identified
Why is Dark Web So Dangerous?

As we mentioned before, the Dark Web is a part of the internet that is not indexed by standard search engines and can only be accessed through special browsers that allow for anonymous browsing. While the Dark Web does contain some legitimate and useful services, it is also home to a variety of illegal and dangerous activities.
Here are some reasons why the Dark Web can be so dangerous:
Anonymity: The Dark Web allows users to remain anonymous and untraceable, making it a haven for criminals who want to carry out illegal activities without being caught.
Illegal Activities: The Dark Web is home to a wide range of illegal activities, including drug trafficking, weapons sales, and human trafficking.
Cybercrime: The Dark Web is also a hub for cybercrime, with websites offering services such as hacking tutorials, stolen credit card information, and malware.
Phishing Scams: Dark Web marketplaces and websites are also rife with phishing scams, which can trick users into providing personal information or sending money to criminals.
Risk of Malware: Many websites on the Dark Web contain malware, which can infect users’ devices and compromise their personal information.
Difficulty in Prosecution: The anonymous nature of the Dark Web makes it difficult for law enforcement to identify and prosecute criminals who operate on the platform.
Overall, the Dark Web can be a dangerous place for individuals who are not experienced in navigating it safely. It’s important to take steps to protect your personal information and avoid engaging in any illegal or suspicious activity when accessing the Dark Web.
Deep Web vs Dark Web

While the terms “Deep Web” and “Dark Web” are often used interchangeably, they actually refer to different things. Here is a comprehensive explanation of the difference between the Deep Web and the Dark Web –
Deep Web –

The Deep Web refers to the portion of the internet that is not indexed by standard search engines, meaning that it cannot be found through a simple Google search. This includes any web page or content that is behind a password-protected login, as well as any content that is not linked to other websites. The Deep Web can include anything from online banking sites and private databases to email and social media accounts.
Dark Web –

The Dark Web, on the other hand, is a part of the Deep Web that is intentionally hidden and cannot be accessed through standard web browsers. Instead, it requires the use of special software, such as Tor, to access. The Dark Web is intentionally designed to be anonymous, with users able to remain untraceable and communicate without being identified.
The Dark Web is often associated with illegal activities, such as drug trafficking, weapons sales, and human trafficking, but it also includes legitimate services, such as anonymous communication channels and privacy protection tools.
Here are the key differences between the Deep Web and the Dark Web –
| Deep Web | Dark Web |
| The portion of the internet not indexed by search engines | Part of the Deep Web requires special software to access |
| Includes password-protected pages, email and social media accounts, private databases | Often associated with illegal activities, but also includes legitimate services |
| Not intentionally hidden | Designed to be anonymous and untraceable |
| Accessible to anyone with appropriate login credentials | Requires specialized knowledge and software to access |
What are the Laws Related to Dark Web in India?

The use of the Dark Web is legal in India as the Government of India does not recognize accessing the space in itself as an illegal activity. For the authorities, it is just another part of the internet that you are surfing, through TOR, Freenet, etc.
However, this doesn’t mean you are free to do whatever you want. You should undoubtedly maintain a few limits while using the dark web. There are several laws related to the use and regulation of the Dark Web and what activities the users are indulging in. Some of the key laws related to Dark Web activities in India are –
- Information Technology Act, 2000: The Information Technology Act is the primary legislation governing cyber crimes and other digital activities in India. It includes provisions for the regulation of the internet, electronic commerce, and the use of digital signatures.
- Prevention of Money Laundering Act, 2002: This act is aimed at preventing money laundering and terrorist financing activities.
- Narcotic Drugs and Psychotropic Substances Act, 1985: This act is aimed at controlling the production, sale, and use of narcotic drugs and psychotropic substances.
- Indian Penal Code, 1860: The Indian Penal Code is the primary criminal code in India, and includes provisions for the punishment of a wide range of offences, including those related to cyber crimes, fraud, and other illegal activities.
- The Unlawful Activities (Prevention) Act, 1967: This act is aimed at preventing unlawful activities that threaten the security of the country.
10 Best Dark Websites You Won’t Find on Google

Here’s a list of the 10 best Dark Web websites you won’t be able to access on Google –
| Website Name | Purpose |
| The Hidden Wiki | Directory for dark web links |
| DuckDuckGo | Go to search engine on the Tor browser |
| Access to Facebook in restricted places | |
| Hidden Answers | Share insights, ask questions and more |
| ProPublica | Investigative journalism platform |
| SecureDrop | The exchange between news outlets and their anonymous sources |
| Keybase | Secure file sharing on the dark web |
| ZeroBin | Share encrypted text on the dark web |
| Riseup | Secure email service primarily for activist groups |
| The Hidden Wallet | Digital wallet for cryptocurrencies |
How to Save Yourself from Hackers?

The internet has brought with it many benefits, but it has also opened up new avenues for hackers to gain access to our personal information and sensitive data. Here are some tips on how to save yourself from hackers:
Use Strong Passwords: Create strong and unique passwords for all your online accounts. A strong password should be at least 12 characters long, and include upper and lowercase letters, numbers, and symbols. Do not use the same password for multiple accounts.
Use Two-Factor Authentication: Two-factor authentication is a security measure that requires a user to provide two forms of identification before accessing an account. This could be a password and a security code sent to your phone, for example. Many online services now offer two-factor authentication, and it’s an effective way to protect your accounts from hackers.

Keep Your Software Updated: Keep your operating system, software, and apps up-to-date with the latest security patches and updates. This will help protect your system from known vulnerabilities that hackers can exploit.
Be Careful What You Click On: Do not click on suspicious links or download attachments from unknown sources. These links and attachments could contain malware or viruses that can compromise your system and steal your data.
Use a Virtual Private Network (VPN): A VPN encrypts your internet traffic, making it more difficult for hackers to intercept your data. It also masks your IP address, making it harder for hackers to track your online activity.
Use Antivirus Software: Antivirus software can detect and remove malware and viruses from your system. Make sure you have up-to-date antivirus software installed on your computer and run regular scans to keep your system clean.
Be Cautious with Personal Information: Be cautious about what personal information you share online, and avoid sharing sensitive information such as your social security number, financial information, or passwords.
By following these tips, you can help protect yourself from hackers and keep your personal information and sensitive data safe online.
FAQs
Q1. What do the statistics say on the usage of the dark web in India?
Answer. India has the biggest marketplace of dark web users as compared to Australia and South America. India makes up 26% of all the country’s users using the dark web.
Q2. What are some examples of Dark Web hacks?
Answer. According to ZDNet, a hacking group known as ShinyHunters tried to sell the data of 73 million users on the dark web. It breached the security of around ten organizations, including online dating app Zoosk, Printing service Chatbooks, South Korean fashion platform Social Share, etc. According to a Cybersecurity firm Cyble, around half a million zoom accounts were hacked in April 2020 and were sold at less than one rupee each. Arxiv found out that around 70.6% of users were male who used the dark web as compared to only 29.4% of females using the dark web. According to the Arxiv, If we take the category-wise statistics, we can summarise it as below from the table.
Q3. Who created the dark web?
Answer. The dark web was created by the US government to communicate with their spies without the risk of being tracked in the process. In 2002, the Tor (or The Onion Router) technology used for the dark web was made available to the general public.
Q4. Do cybercriminals want my data? And how much is it worth?
Answer. Cybercriminals hacking into company databases and stealing user data is very common. You have probably heard of these data breaches in the news. While each piece of data (like a credit card number) might only be worth a few dollars when they resell it, this adds up when they’ve stolen thousands or hundreds of thousands of pieces of sensitive information.
Q5. Who is impacted by the dark web?
Buyers and sellers flock to the dark web because they can trade credit card data, log-in information, forged documents, pirated videos, hacking services, drugs, weapons and stolen company data. The buying and selling of these goods and services are illegal in most countries.
Q6. What is Tor?
Answer. The Tor network enables anonymous communication, and was originally called “The Onion Router”. Tor is what people often mean when they talk about the Dark Web. Tor protects your identity via a process called onion routing, which wraps your data in encrypted layers like an onion. Your traffic is encrypted and relayed three times as a Tor circuit, using randomly-chosen nodes from thousands of volunteer-run servers known as Tor relays. Though Tor circuits can provide a connection to “onion services”, which are generally considered the largest component of the Dark Web, the majority of users only use Tor to access clear Internet services and websites anonymously.
Q7. What is I2P?
Answer. The Invisible Internet Project (I2P) is an anonymity network that focuses on its role as a darknet, not on sending traffic from the clear Internet through it. In this way, it is distinct from Tor, but that’s not the only difference.
8)What Is Cybersecurity?
Ans)Cybersecurity is critical for businesses of all sizes. These 18 tips can help you secure your computers and mobile devices from malicious actors.
* Hackers are criminals who gain unauthorized access to a network and devices, usually with the intent to steal sensitive data, such as financial information or company secrets.
* You can protect your computers by using firewalls and antivirus software and by following best practices for computer use.
* You can protect your mobile devices by turning off Bluetooth when it’s not in use, being mindful of the Wi-Fi networks you connect to and using security applications to improve monitoring and protection.
The growth of the World Wide Web in the 1990s introduced new possibilities and spawned new industries, but it also brought about new downsides of connectivity. Tons of spam started to infiltrate email accounts, and computer viruses wreaked havoc on business networks.
A new threat known as computer hacking extended the definition of thievery to include infiltrating your computer, stealing personal information, tricking you into revealing private data, and using that data to steal and extort personal information, such as business secrets, bank account credentials and even people’s identities
9)What are computer hackers?
Ans)Computer Hackers are people who break into internet-connected devices such as computers, tablets and smartphones, usually with the intent to steal, change or delete information.
Just as other thieves have malicious intent, hackers usually find their way into devices for negative purposes. (However, one exception is so-called white Hat hackers whom companies hire to break into their devices to find security flaws that need to be fixed.) Hackers may want to steal, alter or delete information in your devices, and they often do so by installing malware (software used for malicious purposes) you might not even know is there. These thieves might get access to your most precious data before you’re aware of a break-in.
Key takeaway: Hackers are interested in gaining unauthorized access to your devices to steal sensitive data.
Types of hacking
Here are some of the reasons computer hackers break into devices:
* Financial crimes. We’ve all heard the classic story of somebody checking their credit card statement, only to find transactions they didn’t make. These false transactions are often the result of computer hackers stealing your credit card numbers, checking account info or gaining access to other financial data.
* Vandalism. Hacking has its own subculture, so some hackers may want to vandalize certain websites just to show off to other hackers. Does it sound ridiculous? Don’t make the mistake of not taking this motivation seriously; it’s fairly common, according to malware bites .
* Hacktivism. This portmanteau describes a form of hacking somewhat like vandalism. Some hackers may want to alter or destroy certain websites for politically motivated reasons.
* Corporate espionage. Spying existed long before the internet era, and hacking has only made espionage more accessible to the everyday person. With much of the world constantly connected to the internet, one company can hack into other companies’ devices to steal their information and use it to build an unfair competitive advantage.
Key takeaway: Hackers have a variety of motivations, ranging from financial gain to political goals. Awareness of these intentions can help you anticipate attacks that could affect your small business.
10)How to secure your computer from hackers
Ans)Despite the prevalence of computer hackers, most businesses rely on the internet to track their financials, order and maintain inventory, conduct marketing and PR campaigns, connect with customers, engage in social media, and perform other critical operations.
Yet we continue to hear about massive computer breaches, even at giant corporations with robust security measures in place.
Small businesses are often targeted as well, especially because they may underestimate the risk of cybercrime and may not have the resources to employ expensive cybersecurity solutions. Follow these tips to protect your devices and safeguard your sensitive data:
1. Use a firewall.
Windows and macOS have built-in firewalls – software designed to create a barrier between your information and the outside world. Firewalls prevent unauthorized access to your business network and alert you to any intrusion attempts.
Make sure the firewall is enabled before you go online. You can also purchase a hardware firewall from companies such as Cisco, Sophos or Fortinet, depending on your broadband router, which also has a built-in firewall that protects your network. If you have a larger business, you can purchase an additional business networking firewall.
2. Install antivirus software.
Computer viruses and malware are everywhere. Antivirus programs such as Bitdefender, Panda Free Antivirus , Malwarebytes ,Avast your computer against unauthorized code or software that may threaten your operating system. Viruses may have easy-to-spot effects – for example, they might slow your computer or delete key files – or they may be less conspicuous.
Antivirus software plays a major role in protecting your system by detecting real-time threats to ensure your data is safe. Some advanced antivirus programs provide automatic updates, further protecting your machine from the new viruses that emerge every day. After you install an antivirus program, don’t forget to use it. Run or schedule regular virus scans to keep your computer virus-free.
3. Install an anti-spyware package.
Spyware is a special kind of software that secretly monitors and collects personal or organizational information. It is designed to be hard to detect and difficult to remove and tends to deliver unwanted ads or search results that are intended to direct you to certain (often malicious) websites.
Some spyware records every keystroke to gain access to passwords and other financial information. Anti-spyware concentrates exclusively on this threat, but it is often included in major antivirus packages, like those from Webroot, McAfee and Norton.Anti-spyware packages provide real-time protection by scanning all incoming information and blocking threats.
4. Use complex passwords.
Using secure passwords is the most important way to prevent network intrusions. The more secure your passwords are, the harder it is for a hacker to invade your system.
More secure often means longer and more complex. Use a password that has at least eight characters and a combination of numbers, uppercase and lowercase letters, and computer symbols. Hackers have an arsenal of tools to break short, easy passwords in minutes.
Don’t use recognizable words or combinations that represent birthdays or other information that can be connected to you. Don’t reuse passwords, either.
Also Read –https://www.mymobileindia.com/a-handbook-to-access-the-dark-web/
Also Read – https://www.mymobileindia.com/twitter-data-breached-40-crore-twitter-users-sold-on-dark-web/
Also Read – https://www.mymobileindia.com/mobile-phones-are-an-ideal-target-for-data-privacy-threats
