With smartphones becoming our go-to device for almost every activity, chances of falling prey to a cyberattack cannot be ruled out. Although it’s not your only threat point in today’s digital world as we are also surrounded by / or dependent on a number of other smart devices, the issue of cyber threat / attack has taken a monstrous shape and that calls for an immediate attention to be on our guard. Kunal Bajaj, Chief Business Officer, eSec Forte Technologies, in a conversation with Ramesh Kumar Raja, speaks more about this issue the world is facing today and the services it provides with the integration of new technologies. Excerpts:
Data security is said to be as essential as national security in today’s smart world. How do you look at its current situation in India, especially when mobile phones are there in every hand?
Data security has gained prominence in the backdrop of widening internet connectivity and affordable mobile handset devices. India, with its 1.3 billion population, is at the cusp of the digital revolution, which along with huge opportunities also comes with its own share of challenges.
The most crucial issue among these challenges is related to data security. Specifically in India, the issue is contentious as we lack solid and robust cybersecurity law, although some progress has been made recently on this front. Experts suggest that it’s absolutely essential for all the stakeholders to work together to build an ecosystem that will help curb the menace of a data breach, infringement of privacy, and leakage of sensitive information.
It is heartening to witness that the government has started working on the sensitive issue with serious intent and the proposed Personal Data Protection (PDP) Bill 2021 can be considered a step in the right direction.
There is a global hullabaloo on Pegasus. How do you look at its implications in India? What needs to be done to avoid such incidents?
Incidents of privacy breach and recording of sensitive information using the Pegasus software is just the tip of the iceberg. In actual sense, these events point toward a larger issue that both industry and regulators need to address at a very grassroot level.
In India too, there are allegations and counter-allegations by the political leaders of their phone tapping using the same Pegasus software, although nothing concrete has come to the fore – at least for now. However, if we consider the brighter side of these infamous incidents then we can utilise this as an opportunity to strengthen our cybersecurity laws and come up with a system to provide superior protection to the users’ privacy.
In order to avoid the recurrence of such incidents, it is absolutely essential to have comprehensive data protection and privacy preservation laws in place. As mentioned above, the industry and the regulators have already been working on building a superior system of tracking the leaked information. Further, by providing legal teeth to the framework the crimes in the space of cybersecurity can be reduced considerably. In addition to the legal recourse, spreading awareness about data security and its existing provisions can also prove helpful in reducing the instances of data breaches among the masses.
| “There are allegations and counter-allegations by the political leaders of their phone tapping using the same Pegasus software, although nothing concrete has come to the fore – at least for now. However, if we consider the brighter side of these infamous incidents then we can utilise this as an opportunity to strengthen our cybersecurity laws and come up with a system to provide superior protection to the users’ privacy” |
eSec Forte has created a niche for itself in providing cybersecurity solutions across sectors. Which is the fastest and strongest growing platform for you in today’s time, especially when mobile devices have almost dwarfed PCs, and iOS and Android have made their significant places?
The tremendous appeal and the growth in the mobile handset category have proved to be a game-changer for the digital revolution. eSec Forte offers a number of services under different platforms such as Managed Security Services, Transformation Services, Compliance Management Services, and Security Assessment Services among others.
All these platforms are very well received by clients cutting across industries and specifically, in the area of compliance management and security assessment, the organisation is witnessing tremendous growth and unprecedented response. The trend is aligned with the changing needs of the consumers where the use of mobile phones is becoming increasingly prominent, even dwarfing the desktops, laptops, tablets, etc.
How has been the response to the services that you provide?
Our services are very well-received by the clients cutting across segments and this has become specifically true in case of the data managed security services and transformation services. Even the compliance management system is increasingly finding approval among the clients in the wake of changing circumstances.
Rapid adoption of Cloud and IoT technologies are resulting in growing complexities pertaining to data security, network infrastructure, and security regulation & compliance, thereby boosting demand for cybersecurity solutions and services across the country. What’s your take on this especially when threat points have increased?
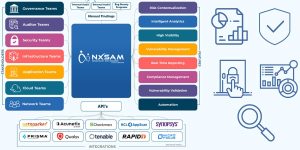
Looking at the multifaceted issues related to cybersecurity, we have adopted a holistic and all-encompassing safety approach to our solutions. eSec Forte has been involved in building one-stop solutions for companies related to their all internet safety and security needs. All our solutions related to Security Services, Transformation Services, Compliance Management Services, and Security Assessment Services are comprehensively built keeping in mind the broader safety challenges associated with the sector. The distinguishing characteristic of our services is the inbuilt safety mechanism that ensures that all concerns related to data management and privacy are addressed comprehensively.
Artificial intelligence and machine learning are said to be the new disruptors in the tech world. Are you adopting these technologies?
Absolutely, yes! In fact, we have already started integrating artificial intelligence (AI) and machine learning (ML) into our products and services. Both of these new-age innovations are very conducive to planning, implementation, diagnosing, and controlling various aspects of cybersecurity solutions and we have received absolutely phenomenal results from this integration. In the coming times, we are further going to step up the level of integration and make AI and ML an integral part of our solutions.
What are the areas of growth for eSec Forte in the country?
While there are many avenues for growth, we are specifically focusing on compliance and security assessment services. Both of these segments are witnessing unprecedented growth and with enhanced digitalization in place, the challenges related to compliance management and security assessment are bound to increase. Keeping in mind this future scenario, we have intensified our efforts and put more investment to come up with advanced solutions on both these fronts.
Other players such as Quick Heal, McAfee, Norton, etc. too have aggressive plans for India. What will be your strategy to be a leader in the market?
In a country like India, competitive intensity is always going to be on the higher side. This is the fact and we fully acknowledge and recognise this reality. In order to be a number one player in our segment, we have specifically started focusing on providing holistic solutions for all customer needs relating to cybersecurity and internet safety management.
Our constellation of products and services is unique and comes with a number of distinguishing parameters that are superior to rival offerings. Further, we exercise the highest level of customer-centricity and our responsive customer care cell ensures that all queries of our clients are addressed quickly without any delay.
Can you please tell us about the security trends that will dominate the market in 2022?
As mentioned above, the integration of artificial intelligence and machine learning will become one of the dominant trends this year. In addition, threats related to Cloud Security and mobile devices will dominate the scenario of cybersecurity solutions. Further, the industry will continue to witness a surge in investment to provide solutions against data breaches, manual intervention errors, and targeted ransomware among others.
| “The integration of artificial intelligence and machine learning will become one of the dominant trends this year. In addition, threats related to Cloud Security and mobile devices will dominate the scenario of cybersecurity solutions. Further, the industry will continue to witness a surge in investment to provide solutions against data breaches, manual intervention errors, and targeted ransomware among others” |
What are the challenges that eSec Forte foresees?
There are many challenges that both our organisation and industry at large have to contend with in the coming times. One of the biggest challenges is to keep up pace with the constantly changing business environment and come up with innovative solutions aligned with the needs of clients and the industry. The threats related to privacy and data security are also on the rise which mandates the upgradation of the current solutions available commercially in the market. This, in turn, will require more investment in future products which is again a challenge from both financial and technical perspectives. In addition, there are challenges related to the overall security management and changing nature of the regulatory framework that eSec Forte is preparing to handle in the future.
Also Read: “Mobile phones are an ideal target for data privacy threats”
Also Read: What Kids Were Looking For During Spring 2022?
Also Read: Russia-Ukraine crisis: Cyber-attack, most common types and how to avoid
