Highlights
- eSIM technology enables digital SIM swapping, exposing users to new fraud risks.
- Attackers use stolen credentials to port victims’ phone numbers to their devices.
- Cybersecurity experts recommend using complex passwords and two-factor authentication.
- Increased eSIM adoption calls for enhanced security measures against cyber fraud.
The introduction of embedded Subscriber Identity Modules (eSIMs) has heralded a new era of convenience and connectivity.
These digital SIM cards, stored directly on a device’s chip, offer a seamless way to maintain cellular service without the physical constraints of traditional SIM cards.
However, this advancement has not come without its pitfalls.
Cybercriminals, ever adaptive, have found ways to exploit eSIM technology to commit fraud, posing a significant threat to user security and privacy.
The Mechanics of eSIM Swapping Scams
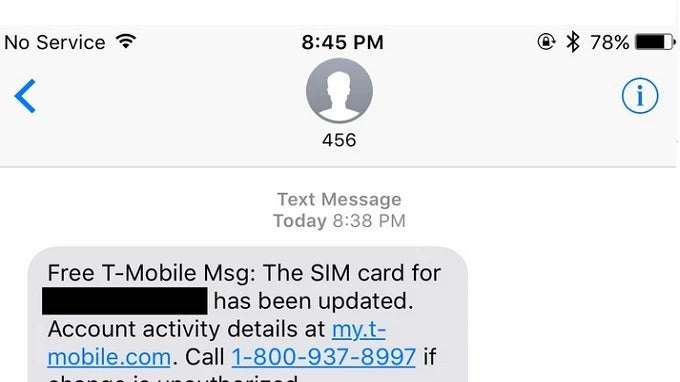
eSIM technology, while revolutionary, has inadvertently provided cyber criminals with a new vector for attack.
As per a press release by Russian outlet Facct, by exploiting the digital nature of eSIM provisioning, attackers can hijack a victim’s phone number and, by extension, gain unauthorized access to their personal and financial accounts.
This type of attack, known as SIM swapping, is not new, but the method of execution has evolved with the advent of eSIMs.
Traditionally, SIM swappers used social engineering tactics or insider assistance to port a target’s phone number to a new device.
However, with increased security measures put in place by mobile carriers, attackers have turned their attention to the vulnerabilities inherent in eSIM technology.
By obtaining a victim’s mobile account credentials through phishing, brute force attacks, or data leaks, they can initiate a number of porting requests to a device under their control.
“Having gained access to the victim’s mobile phone number, cybercriminals can obtain access codes and two-factor authentication to various services, including banks and messengers, opening up a mass of opportunities for criminals to implement fraudulent schemes,” said F.A.C.C.T. analyst Dmitry Dudkov.
This process involves generating a QR code that, once scanned, reprograms the eSIM, effectively transferring the victim’s phone number to the attacker’s device.
Countermeasures and Recommendations

The shift to eSIM technology, while convenient, necessitates heightened vigilance and enhanced security measures to protect against these sophisticated attacks.
Cybersecurity experts advocate for the adoption of complex, unique passwords for cellular service accounts and the activation of two-factor authentication wherever possible.
For accounts holding sensitive information, such as banking or cryptocurrency wallets, additional layers of security, including physical security keys or authenticator apps, are recommended.
FAQs
What is eSIM fraud?
eSIM fraud occurs when cybercriminals hijack a person’s phone number by exploiting the digital SIM technology (eSIM), allowing them to gain unauthorized access to the victim’s personal and financial accounts.
How do attackers carry out eSIM swapping?
Attackers perform eSIM swapping by acquiring a victim’s mobile account credentials through methods like phishing, then generate a QR code to transfer the phone number to a device they control.
Why is eSIM fraud becoming more common?
The increasing popularity of eSIM technology for its convenience and functionality has inadvertently opened up new avenues for cybercriminals to exploit, leading to a rise in eSIM fraud incidents.
What can individuals do to protect themselves from eSIM fraud?
To safeguard against eSIM fraud, individuals should use unique, complex passwords for their cellular accounts, enable two-factor authentication, and consider additional security measures for sensitive accounts.
Are there any specific recommendations for securing financial accounts against eSIM fraud?
For financial accounts, it is advisable to use physical security keys or authenticator apps, which provide a higher level of security compared to traditional SMS-based two-factor authentication methods vulnerable to eSIM fraud.
How to convert Airtel SIM to e-SIM?
- Send an SMS – “e-SIM<>registered email id” to 121.
- Confirm the initiation process by replying back with “1”.
- After confirmation, Airtel will send you an SMS asking you to provide consent over a call. Authenticate your ID over the call.
- After the authentication, you will receive a QR code on your registered email ID.
- Scan that QR code to enable e-SIM services.
- Your eSIM will be activated in around 2 hours.
How to convert Vodafone-idea SIM to e-SIM?
- SMS e-SIM< space >registered email ID to 199.
- Confirm your request by replying “E-SIMY”.
- Give your consent over a call.
- Next, you will receive SMS with the QR Code for e-SIM activation on your registered email ID.
How to convert Jio SIM to e-SIM?
- Type “GETE-SIM <32 Digit EID><15 Digit IMEI>” and send SMS to 199.
- To get IMEI number type *#06# and send.
- To get the EID number go to Settings> About phone > and find “EID.”
- You will receive a 19-digit virtual eSIM number via SMS and registered email ID.
- Notably, if you have not registered your email ID with your existing telecom operator, you will be asked first to update the email and then reinitiate the eSIM process.
Now, after getting the eSIM number, send another SMS “SIMCHG <19 digit e-SIM Number>” to 199.
Jio will send you an update on eSIM procession within 1-2 hours. It will take around 1-2 hours.
Next, type “1” and send an SMS to 183 to request an automated call from +91 2235072222. On the call, dial ‘1’ to confirm.
Once the process is completed, you can go to the eSIM setting on the smartphone and tap on install ‘Data plan’ to activate your eSIM.
Make sure your phone is connected to mobile data/Wi-Fi during the process.
On iPhone, go to Settings > Mobile Data > Add Data Plan > Scan QR code > e-SIM.
How to change your SIM to eSIM ?
To convert your eSIM first check if your smartphone supports eSIM and if your telecom operator provides eSIM facility. As for Jio, Airtel, and Vodafone-Idea, the telecom operator offers e-SIM at no additional cost.
What is Social media’s role in SIM swap fraud ?
Scammers can use your social media profiles to gather information on you that may help them impersonate you when they’re trying to close a SIM swap scam.
What are the Signs that you’re the victim of a SIM swap?
1. You can’t make calls or send texts
Getting errors when trying to send texts or make calls? The first sign that you could be a victim of SIM swapping is when your phone calls and text messages aren’t going through. This likely means fraudsters have deactivated your SIM card and are using your phone number.
2. You’re notified of activity elsewhere
You’ll know you’re a victim if your phone provider notifies you that your SIM card or phone number has been activated on another device.
3. You’re unable to access accounts
If your login credentials no longer work for accounts like your bank and credit card accounts, it’s likely that scammers have changed your passwords and usernames, maybe after having taken over your phone number. Contact your bank and other organizations immediately to let them know.
4. You find transactions you don’t remember making
If you’re checking your online credit card statement and you notice several transactions that you don’t remember making, you might be the victim of a SIM swap scam. This is a sign that criminals have accessed your credit card number and used it to make unauthorized purchases.
They might have done this by first stealing your phone number and using the information sent to it to access your account.
How can you protect against SIM swap scams?
Fortunately, there are ways in which you, and your service providers, can help protect against becoming a victim of SIM swap fraud.
Online behavior: Beware of phishing emails and other ways attackers may try to access your personal data to help them convince your bank or cell phone carrier that they are you.
Don’t click on links in email messages from people you don’t know. And remember, yourbank, cable provider, credit card company, or other service providers won’t ask for your personal or financial information through an email message.
Account security: Boost your cellphone’s account security with a unique, strong password and strong security questions and answers that only you know.
PIN codes: If your phone carrier allows you to set a separate passcode or PIN for your communications, consider doing it. It could provide an additional layer of protection.
IDs: Don’t build your security and identity authentication solely around your phone number. This includes text messaging (SMS), which is not encrypted.
Authentication apps: You can use an authentication app such as Google Authenticator, which gives you two-factor authentication but ties to your physical device rather than your phone number.
Bank and mobile carrier alerts: See if your banks and mobile carrier can combine efforts, sharing their knowledge of SIM swap activity, and implementing user alerts along with additional checks when SIM cards are reissued, for instance.
Behavioral analysis technology: Banks can use technology that analyzes customer behavior to help them discover compromised devices, warning them not to send SMS passwords.
Call-backs: Some organizations call customers back to make sure they are who they say they are — and to catch identity thieves.
Also Read: How online identity verification can help MNOs reach the full potential of eSim technology
Also Read: IDEMIA, Microsoft collaborate to provide next-gen eSIM Connectivity services
